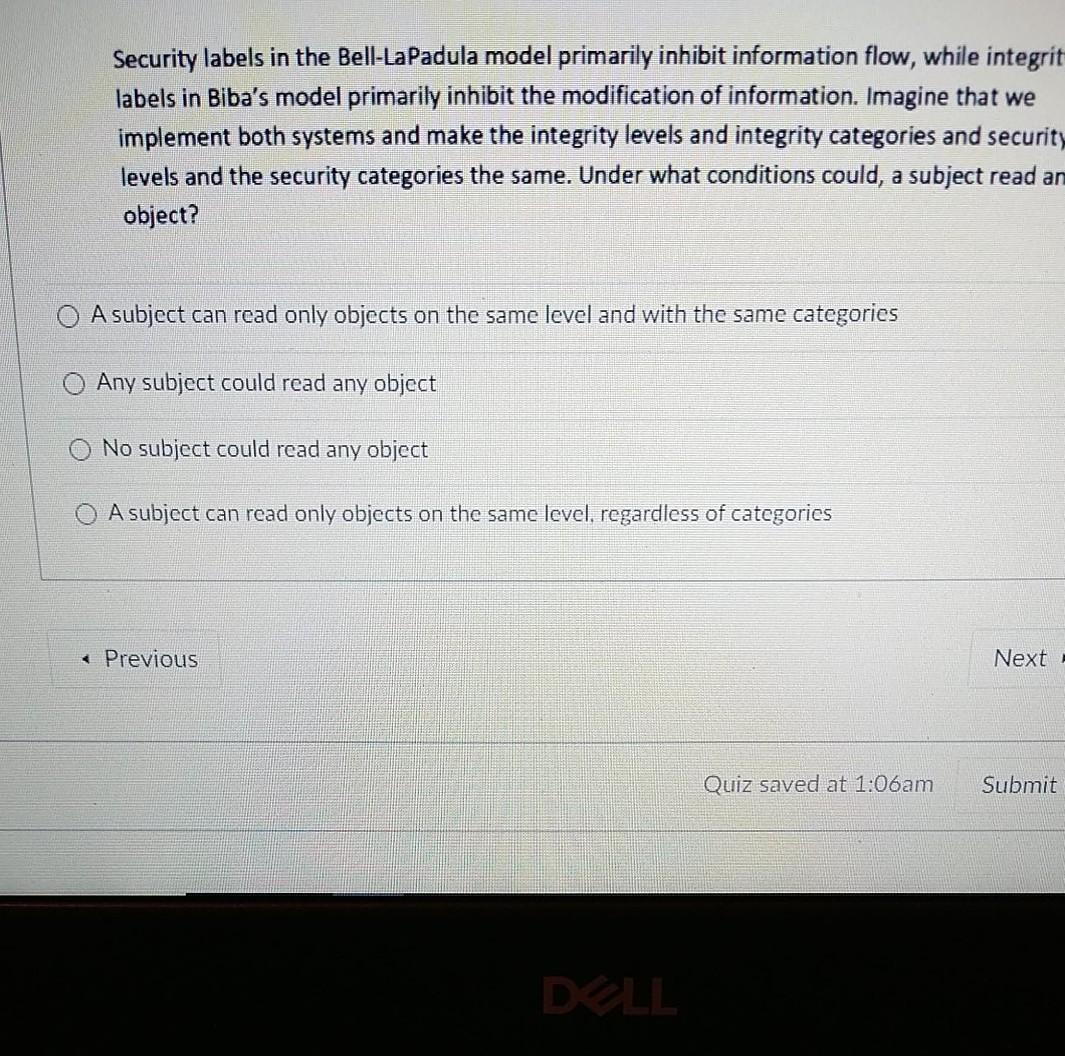
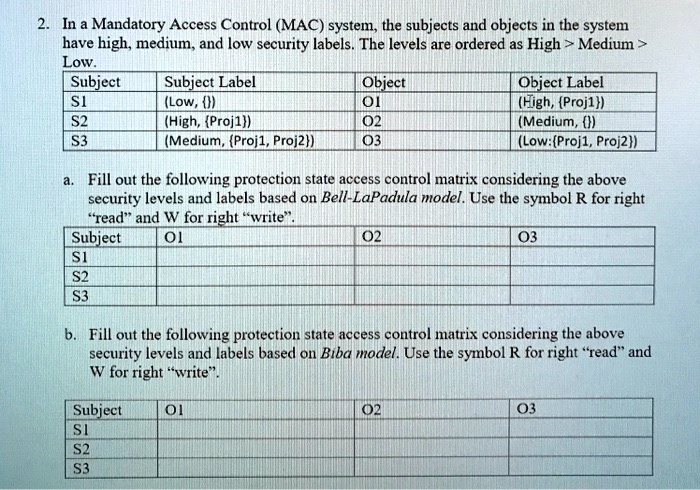
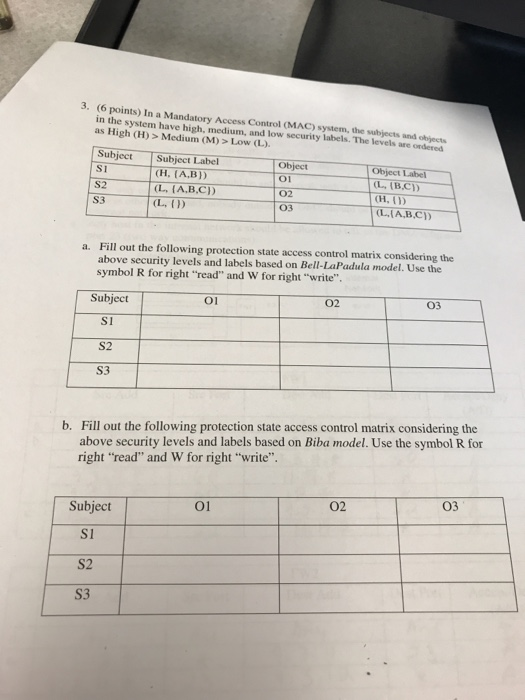
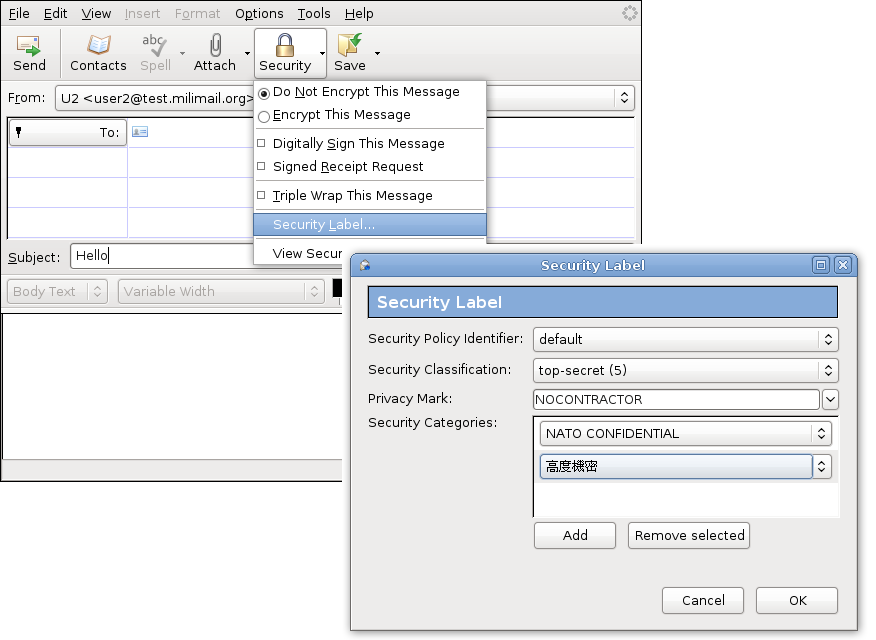
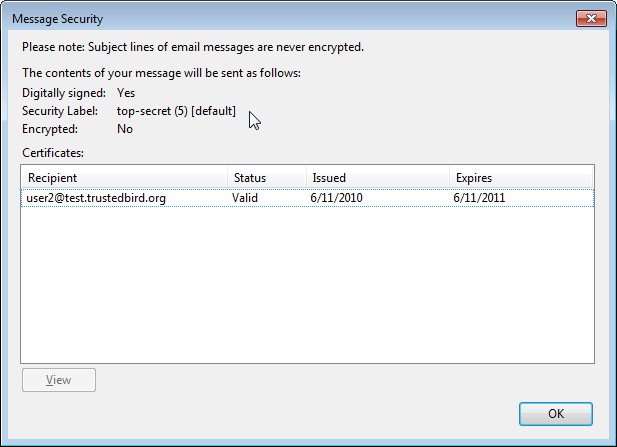
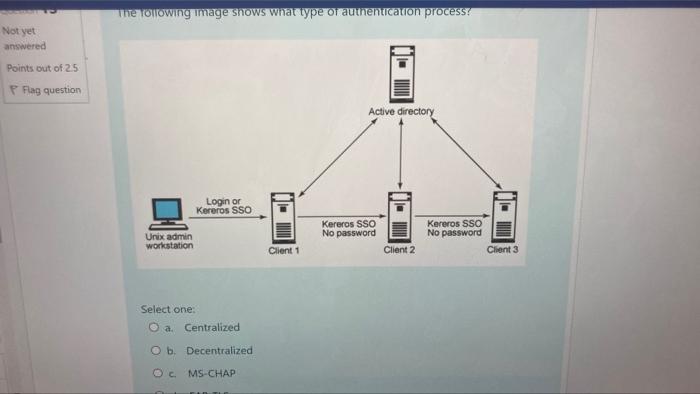
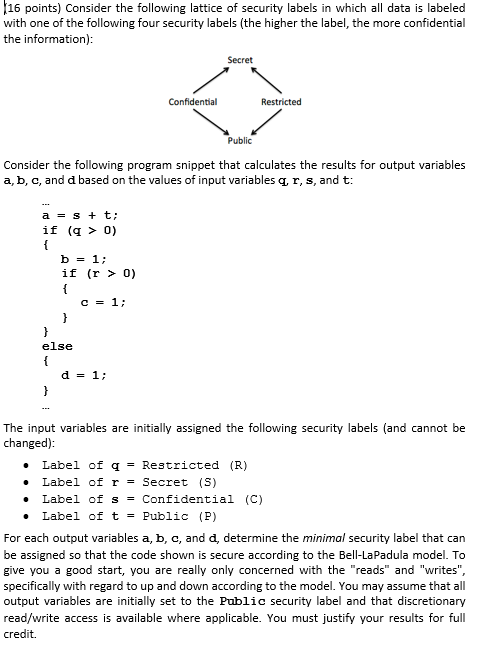
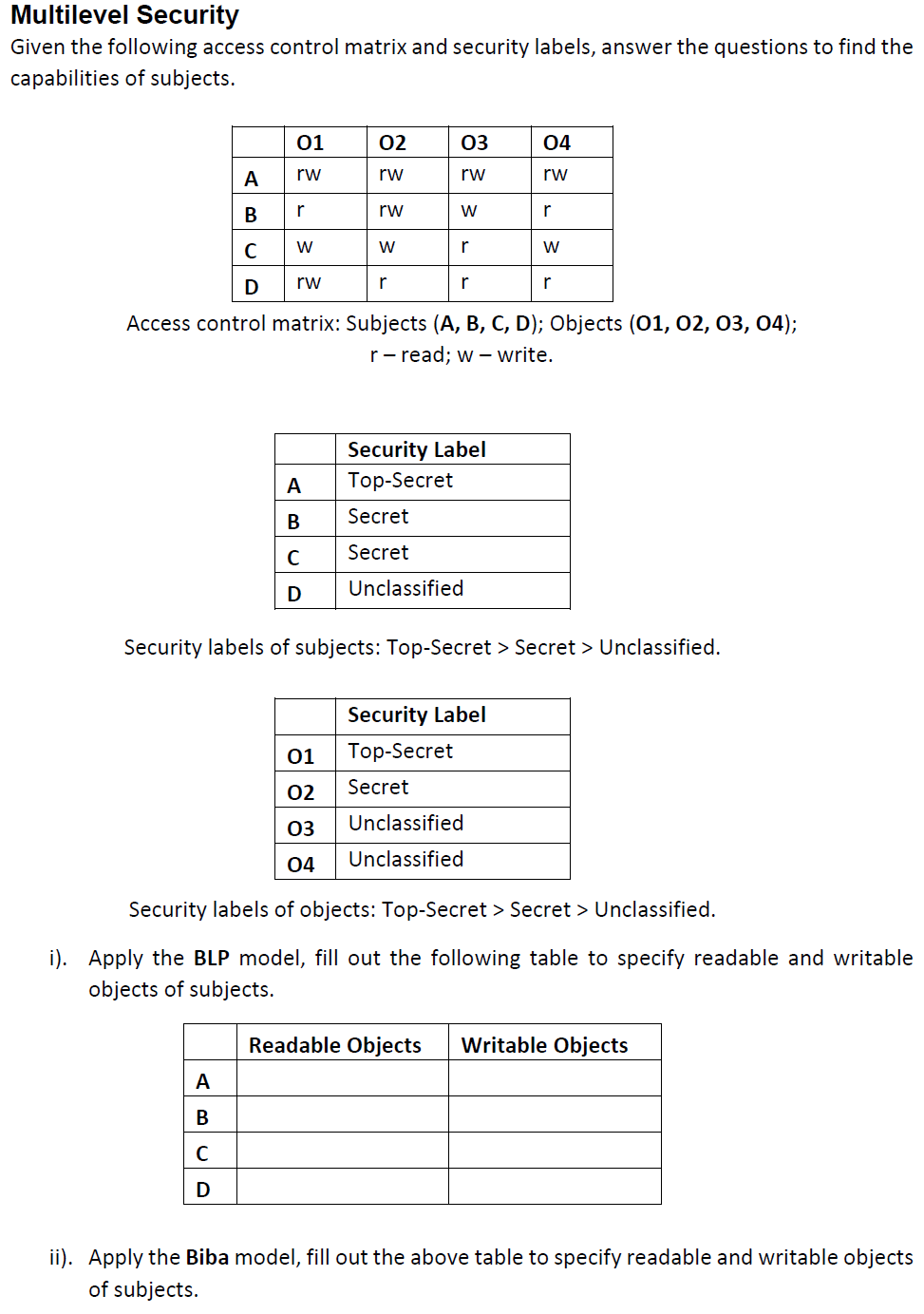
45 security labels are used in what type of model
docs.docker.com › compose › compose-fileCompose specification | Docker Documentation But the actual definition involves distinct platform resources and services, which are abstracted by this type. A Secret is a specific flavor of configuration data for sensitive data that SHOULD NOT be exposed without security considerations. Secrets are made available to services as files mounted into their containers, but the platform ... Introduction To Classic Security Models - GeeksforGeeks 11.07.2022 · There are 3 main types of Classic Security Models. Bell-LaPadula ; Biba; Clarke Wilson Security Model; 1. Bell-LaPadula . This Model was invented by Scientists David Elliot …
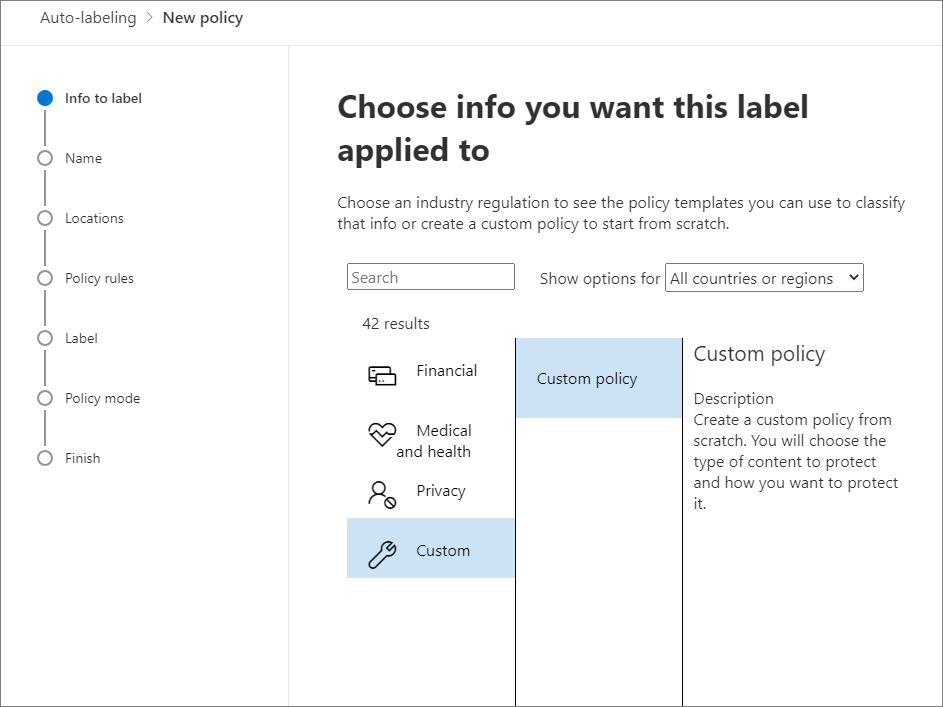
Sensitivity Labels: What, Why and How - nBold 06.10.2021 · Open Microsoft 365 Security & Compliance Center, go to Classification and select Sensitivity labels from the dropdown. Click Create a label and fill in all the necessary …

Security labels are used in what type of model
› en-us › microsoft-365Microsoft 365 Roadmap | Microsoft 365 The Microsoft 365 roadmap provides estimated release dates and descriptions for commercial features. All information is subject to change. As a feature or product becomes generally available, is cancelled or postponed, information will be removed from this website. Security Models | CISSP Exam Cram: Security Architecture … Access Control using Security Labels & Security Clearance … Security Labels are generally specified by the standard that uses them. There are two compatible specifications of Security Labels in wide use: ESS Security Labels are defined in the Internet …
Security labels are used in what type of model. jmeter.apache.org › usermanual › component_referenceApache JMeter - User's Manual: Component Reference The SMTP Sampler can send mail messages using SMTP/SMTPS protocol. It is possible to set security protocols for the connection (SSL and TLS), as well as user authentication. If a security protocol is used a verification on the server certificate will occur. Two alternatives to handle this verification are available: Trust all certificates › ictU.S. Access Board - Revised 508 Standards and 255 Guidelines The U.S. Access Board is a federal agency that promotes equality for people with disabilities through leadership in accessible design and the development of accessibility guidelines and standards for the built environment, transportation, communication, medical diagnostic equipment, and information technology. en.wikipedia.org › wiki › InternetInternet - Wikipedia To address the issues with zero-rating, an alternative model has emerged in the concept of 'equal rating' and is being tested in experiments by Mozilla and Orange in Africa. Equal rating prevents prioritization of one type of content and zero-rates all content up to a specified data cap. Different Type of Security Tags | Retail Security There are two widely used types of locking mechanisms available; magnetic and mechanical, with magnetic tags available in a series of strengths ranging from standard to SuperLock, …
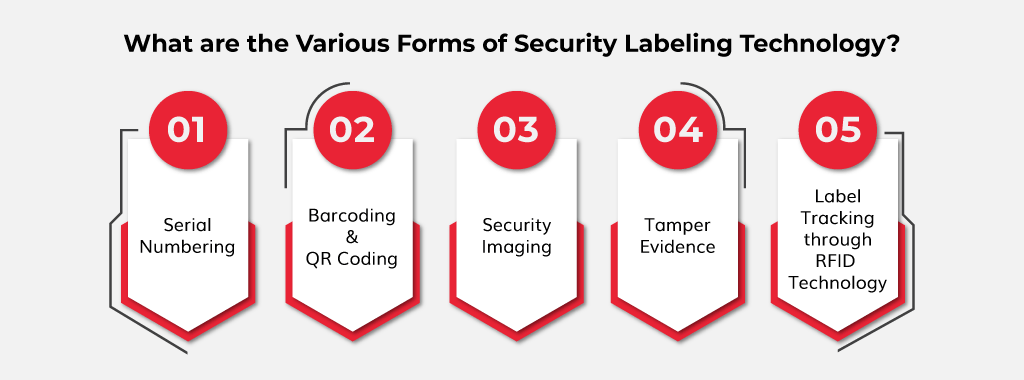
Using Security Labels for Directory Access and Replication … Custom Security and Asset Labels with logos and barcodes Rapid production & shipping of all types of fixed asset labels/tags, tamper-proof security seals (tamper-evident label). With or without logos company logos, custom text, serial numbers, and … Why do we have four levels of security in Power BI? 03.11.2021 · Row-Level-Security (RLS) in Power BI models Row-Level-Security (RLS) controls who has access to which data in the data model. This feature of Power BI is well documented … abcnews.go.com › internationalInternational News | Latest World News, Videos & Photos -ABC ... Oct 18, 2022 · Get the latest international news and world events from Asia, Europe, the Middle East, and more. See world news photos and videos at ABCNews.com
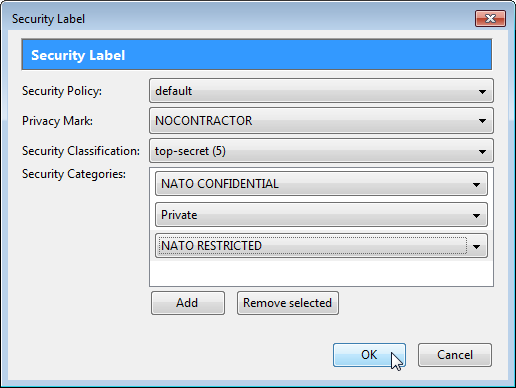
html.spec.whatwg.org › multipage › infrastructureHTML Standard Oct 17, 2022 · An encoding has an encoding name and one or more encoding labels, referred to as the encoding's name and labels in the Encoding standard. 2.1.8 Conformance classes. This specification describes the conformance criteria for user agents (relevant to implementers) and documents (relevant to authors and authoring tool implementers). Which type of access control model assigns security level labels to ... 08.05.2022 · Explanation: Mandatory access control (MAC) assigns security level labels to information and enables users with access based on their security level clearance. This is the … CISSP Questions and Answers -1 Flashcards | Quizlet CISSP Questions and Answers -1. Term. 1 / 25. The Bell-LaPadula access control model is focused on which of the following security properties? Click the card to flip 👆. Definition. 1 / 25. › … Access Control using Security Labels & Security Clearance … Security Labels are generally specified by the standard that uses them. There are two compatible specifications of Security Labels in wide use: ESS Security Labels are defined in the Internet …
Security Models | CISSP Exam Cram: Security Architecture …
› en-us › microsoft-365Microsoft 365 Roadmap | Microsoft 365 The Microsoft 365 roadmap provides estimated release dates and descriptions for commercial features. All information is subject to change. As a feature or product becomes generally available, is cancelled or postponed, information will be removed from this website.

Veltec 2212 Fluorescent Red Pricing Labels for Garvey and Contact 22-6, 22-7, 22-8 Price Gun/Labelers, Free Ink Roller – 9 Rolls, 11,000 Labels with ...





























Post a Comment for "45 security labels are used in what type of model"